top of page

Latest from Bridge Connect
Experience that spans technologies, markets, and continents.
The Role of Confidential Computing in Telecom Security: A Practical Guide
Telecom networks face constant cyber threats, but confidential computing offers a breakthrough in data protection. By securing data during processing through hardware-based encryption and secure enclaves, it shields critical workloads from attack. This practical guide explores how telecom providers can adopt confidential computing to strengthen network resilience, reduce breach risks, and meet rising compliance demands in an evolving digital landscape.

Bridge Connect
Oct 31, 20254 min read
Digital Provenance in Telecom: Building Trust in Supply Chains
Most telecom supply chains still hide where hardware and software originate. Digital provenance changes that, creating verified digital records that trace every step from factory to deployment. By integrating blockchain, encryption, and transparent ledgers, telecom operators can expose hidden risks, meet compliance standards, and strengthen trust across partners — ensuring equipment authenticity and long-term network reliability.

Bridge Connect
Oct 31, 20254 min read
Rethinking Governance: How Edge-First Architecture is Changing the Game
Edge-first architecture is a game-changer in how we manage network systems. It takes the focus away from centralised control and places it closer to where data is actually used. This section will break down the basics of this new approach.

Bridge Connect
Oct 31, 20254 min read
Navigating the New Era of Cyber Attack Attribution: Insights for Telecom and Infrastructure Leaders
Cyber attack attribution has moved beyond simple technical tracing. As attacks become more complex and state actors more involved, your ability to understand new attribution methods and international cyber conflict law shapes strategic decisions. As telecoms and infrastructure advisors, Bridge Connect examines these shifts to help you anticipate risks and respond with clarity amid increasing geopolitical tensions. Understanding Cyber Attack Attribution The landscape of cyber

Bridge Connect
Oct 29, 20255 min read
Building Climate Resilience: Integrating ICT and Critical Infrastructure for Board-Level Strategy
Extreme weather events are no longer rare disruptions—they are testing the resilience of critical infrastructure and ICT systems worldwide. Boards must recognise how climate risks intersect with digital and physical assets to protect operations and investments. As telecoms and infrastructure advisors, Bridge Connect examines how integrating climate resilience into ICT and critical national infrastructure risk frameworks shapes strategic decision-making at the highest level. U

Bridge Connect
Oct 29, 20255 min read
Understanding Cyber-Physical System Vulnerabilities in Critical Infrastructure
Recent cyber incidents targeting critical infrastructure have exposed gaps few expected to see so clearly. Your organisation’s cyber-physical systems face risks that go beyond traditional IT threats, with potential to disrupt essential services and national security. As telecoms and infrastructure advisors, Bridge Connect examines why understanding these vulnerabilities is crucial for boards now, where oversight and strategic action can prevent costly consequences. The Nature

Bridge Connect
Oct 29, 20255 min read
Ensuring Data Privacy in Shared Environments: The Role of Confidential Computing
Data privacy risks escalate as organisations share infrastructure to cut costs and boost agility. Your sensitive information can be exposed during processing, even within trusted cloud environments. As telecoms and infrastructure advisors, Bridge Connect examines how confidential computing offers a new layer of protection, keeping data secure while in use—crucial for boards navigating today’s complex digital landscape. Understanding Confidential Computing What is Confidential

Bridge Connect
Oct 29, 20254 min read
Understanding Zero Trust Architecture: The Future of Defence Cloud Security
Traditional perimeter defences no longer hold firm against today’s cyber threats targeting defence cloud systems. Your organisation’s sensitive data faces relentless pressure from increasingly sophisticated attacks that bypass once-reliable safeguards. As telecoms and infrastructure advisors, Bridge Connect examines how Zero Trust Architecture and sovereign cloud initiatives are reshaping defence security strategies worldwide. This analysis highlights why adopting these appro

Bridge Connect
Oct 29, 20253 min read
Harnessing AI: How Purpose-Built IT Platforms Drive Business Success
AI demands are reshaping IT infrastructure faster than most boards anticipate. Generic platforms struggle to keep pace with AI-intensive workloads, creating risks for businesses aiming to harness this technology effectively. As telecoms and infrastructure advisors, Bridge Connect examines why purpose-built IT platforms tailored for AI are becoming essential for achieving measurable business outcomes. This analysis explains what leadership needs to know now to stay ahead. Unde

Bridge Connect
Oct 29, 20253 min read
Why Federated Data Governance is the Future of Compliance and Agility
Centralised data lakes have long promised streamlined compliance and agility, yet they often fall short under growing regulatory pressure and complex operational demands. Many organisations find themselves wrestling with bottlenecks and rigid controls that slow decision-making and risk management. As telecoms and infrastructure advisors, Bridge Connect examines how federated data governance offers a fresh approach, distributing control to meet compliance while preserving the

Bridge Connect
Oct 29, 20254 min read
Impact of New Cyber Disclosure Rules on Telecoms and Critical Infrastructure
New cyber disclosure rules are reshaping how telecoms and critical infrastructure report threats and breaches. Many leaders face the challenge of adapting their strategies under tighter resilience mandates while maintaining operational stability. As telecoms and infrastructure advisors, Bridge Connect examines what these regulatory changes mean for your organisation’s risk profile and strategic priorities. This analysis will help you navigate evolving obligations and safeguar

Bridge Connect
Oct 29, 20254 min read
The Strategic Edge – Why Quantum Communications Will Reshape Global Power
This is not just tech - it’s power politics. Boards that move early on quantum communications will secure influence, contracts, and competitive edge.

Bridge Connect
Oct 26, 20253 min read
Quantum-Safe Encryption: Preparing Networks Before It’s Too Late
Quantum computing could render today’s digital security obsolete. Boards and executives must act now to prepare networks with quantum-safe encryption, ensuring resilience before the threat becomes unmanageable.

Bridge Connect
Oct 21, 20253 min read
Cyber-Resilience of Terrestrial Networks: Securing the New Ground Layer
Terrestrial timing is the new critical infrastructure frontier. Bridge Connect shows how zero-trust and cyber-resilience can secure the systems replacing GNSS dependence.

Bridge Connect
Oct 21, 20255 min read


AI-Assisted PNT Anomaly Detection: Learning to See the Invisible
AI is giving Gulf nations eyes on invisible GNSS interference. Bridge Connect shows how data fusion and machine learning can predict outages before they happen.

Bridge Connect
Oct 21, 20255 min read

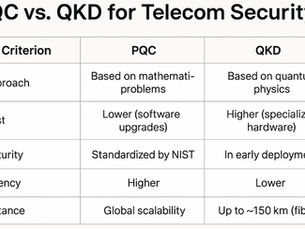
Quantum-Safe Telecom Security: Protecting the Backbone of Digital Economies
Quantum computing is about to shatter classical encryption. Bridge Connect shows boards how to secure telecom networks with PQC and QKD — and why 2025 is the moment to act.

Bridge Connect
Oct 21, 20254 min read


Gulf Reality Check: GNSS Disruption in Qatar and the Wider GCC
When Qatar halted navigation due to a “GPS fault,” it signalled the Gulf’s first major GNSS disruption. Here’s what really happened — and what Gulf boards must do next.

Bridge Connect
Oct 20, 20258 min read


Mapping GNSS Interference: From the Black Sea to the Gulf
Persistent GNSS jamming and spoofing are visible from the Black Sea to the Gulf. Understanding these hotspots is the first step toward a resilient, multi-layer PNT strategy.

Bridge Connect
Oct 20, 20255 min read


GNSS Interference 101: Jamming, Spoofing & Timing Risks
NSS interference isn’t just a navigation problem; it’s a timing problem that can quietly destabilise ports, aviation, telecoms and the grid. Bridge Connect explains how and what to do next.

Bridge Connect
Oct 20, 20255 min read
bottom of page